IIoT Component Security Assurance (ICSA)
Product certification for IIoT Components.
An Industry-Vetted IIoT Certification Program
The ICSA certification is specifically designed for IIoT products and certifies to the industry-leading ISA/IEC 62443 series of international standards.
- Read the press release announcing the ICSA certification
- Read the study: "IIoT Component Certification Based on the 62443 Standard"
- View the webinar: ISASecure ISA/IEC 62443 IIoT Component Security Assurance (ICSA) Certification Launch
ICSA VERSION 1.0.0
IIoT Component Security Assurance (ICSA) - version 1.0.0
Scope
The ISASecure IIoT Component Security Assurance (ICSA) is a security certification program for IIoT devices and IIoT gateways. ICSA certification applies to IACS components that:
- meet the definition in the standard ISA/IEC 62443-4-2 Security for industrial automation and control systems Part 4-2: Technical security requirements for IACS components, for at least one of embedded device, host device, or network device; and
- meet one or both of the following definitions for IIoT device and IIoT gateway:
An IIoT device is an entity that is a sensor or actuator for a physical process, or communicates with sensors or actuators for a physical process, that directly connects to an untrusted network to support and/or use data collection and analytic functions accessible via that network
An IIoT gateway is an entity of an IIoT system that connects one or more proximity networks and the IIoT devices on those networks to each other and directly connects to one or more untrusted access networks
Here following are relevant definitions from the ISA/IEC 62443-4-2 standard:
embedded device special purpose device running embedded software designed to directly monitor, control or actuate an industrial process
host device general purpose device running an operating system (for example Microsoft Windows OS or Linux) capable of hosting one or more software applications, data stores or functions from one or more suppliers
network device device that facilitates data flow between devices, or restricts the flow of data, but may not directly interact with a control process
Untrusted networks ICSA certification was developed for components designed to directly connect with untrusted networks within an overall IIoT system architecture. Untrusted networks include networks accessible to the public, such as the internet or cell networks. They also include, but are not limited to, internal enterprise networks that may not be under the full control of the asset owner responsible for the cybersecurity impact of an IIoT component. These enterprise networks may be controlled by the asset owner’s overall enterprise or by another enterprise such as a partner or vendor.
ICSA addresses component security characteristics and capabilities as well as supplier development practices for IIoT devices and IIoT gateways. ICSA requirements covering these topics are based on parts 4-2 and 4-1 of the ISA/IEC 62443 standard, respectively. (ICSA does not reference the current draft Technical Report ISA-TR62443-4-3, since enumeration of specific IIoT component requirements is not in scope for that report. TR62443-4-3 provides guidance for asset owners applying 62443 for IIoT.)
A component that meets the requirements of the ISASecure ICSA specification will earn the ISASecure ICSA certification; a trademarked designation that provides recognition of product security characteristics and capabilities, and provides an independent industry stamp of approval similar to a ‘Safety Integrity Level’ Certification (ISO/IEC 61508).
ICSA requires that a certified component be developed in accordance with all requirements in ISA/IEC 62443-4-1 Security for industrial automation and control systems Part 4-1: Secure product development requirements. ICSA also requires conformance with five additional development lifecycle sub practices which may be viewed as extensions to 62443-4-1.
The ICSA program defines two certification tiers for a component, offering a Core and Advanced level of security assurance. This structure is an adaptation of the 62443 structure which has four capability security levels. Core tier is based upon capability security level 2 requirements from ISA/IEC 62443-4-2, and Advanced tier on capability security level 4. ICSA program criteria incorporate a relatively small number of exceptions and extensions to the 62443-4-2 technical capabilities standard, to address the IIoT component environment. For example, an IIoT device certified to ICSA Core tier will have been shown to meet:
- All 62443-4-2 capability security level 2 requirements with the exception of two
- Eight 62443-4-2 requirements at 62443-4-2 capability security levels 3 or 4, that strengthen identification/authentication to narrow the field of successful attackers, and strengthen attack monitoring/diagnosis/response capabilities, in recognition of the component’s interface to an untrusted network
- A small set of additional functional capability requirements unique to ICSA, which may be viewed as extensions to 62443-4-2.
ICSA certification tiers and requirements were initially developed as part of a joint study carried out by ISCI and the industry consortium ISA Global Cybersecurity Alliance (ISAGCA). Study recommendations were refined and realized as the ICSA certification program.
ISASecure ICSA is modeled after the ISASecure CSA certification program (Component Security Assurance), which certifies conformance to 62443-4-2 for software applications, embedded devices, host devices, and network devices. Much of the CSA program has been reapplied for ICSA, as the two programs have the majority of their requirements in common. The ICSA specifications ICSA-311 and ISDLA-312 (presented below) highlight differences between the two programs. The ICSA program defines streamlined procedures for a CSA-certified product to obtain ICSA certification.
To strengthen stakeholder confidence in component security over time after initial certification, ICSA incorporates a new process called Security Maintenance Audit. SMA requires a periodic surveillance evaluation of the supplier’s security maintenance practices as applied to an IIoT component holding ICSA certification. In order for an ICSA certified component and its updates and upgrades to maintain that certification over time, the supplier will maintain their SDLA certification as well as good standing under SMA for the certified component.
The elements of an initial ICSA certification are illustrated in Figure 1 below.
In order to obtain ISASecure ICSA certification, a supplier must pass a security development lifecycle process assessment for component development (SDLPA-IC). Based upon this assessment, an ISASecure SDLA process certification is granted as described in SDLA-100. A supplier may already hold an SDLA process certification when they apply for an ICSA certification, or may apply for ICSA and SDLA certification in parallel. Initial ISASecure ICSA certification for IIoT components has three additional elements:
· Security Development Artifacts for IIoT components (SDA-IC);
· Functional Security Assessment for IIoT components (FSA-IC); and
· Vulnerability Identification testing for IIoT components (VIT-IC).
SDLPA-IC and SDA-IC both assess development process. SDA-C examines the artifacts that are the outputs of the supplier’s development lifecycle processes as they apply to the component to be certified. FSA-IC examines the security capabilities of the component, while recognizing in accordance with ISA/IEC 62443-4-2 that requirements for security functionality differ by component type. VIT-IC scans the component for the presence of known vulnerabilities.
Both certification tiers include the certification elements defined in Figure 1. SDLPA-IC does not have an tier. SDA-IC and VIT-IC assessments are the same for both tiers with the exception of allowable residual risk for known security issues. FSA-IC incorporates more requirements for Advanced tier than for Core tier.
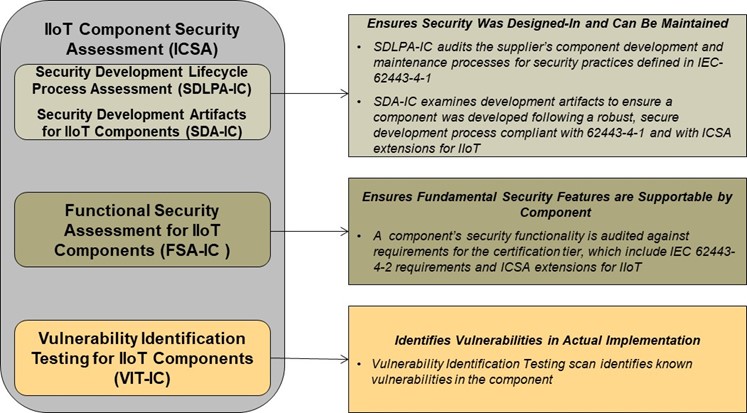
Figure 1 - Evaluation Elements for initial ISASecure ICSA Certification
ISASecure ICSA Conformance Scheme Fees
| ICSA Certification Registration Fee (Annual Fee) | $1,200 |
Component Security Assurance (ICSA) Certification Scheme Description
ISASecure Members receive Scheme Descriptions for FREE. If you are an ISASecure member and are unsure how to access content, please email mritterskamp@isa.org. Please include your company membership information.
| ICSA-100 ISASecure Certification Scheme | View / Download PDF |
| ICSA-102 Baseline Document Versions and Errata | View / Download PDF |
| ISASecure-119 Comparison of ICSA and CSA | Available for Purchase in ISA Store |
Initial Certification and Maintenance of Certification Policies and Criteria
| ICSA-204 Use of Symbols and Certificates | View / Download PDF |
| ICSA-300 ISASecure Certification Requirements | Available for Purchase in ISA Store |
| ICSA-301 Maintenance of ISASecure Certification | Available for Purchase in ISA Store |
| ISASecure-120 Relabeled Policy | Available for Purchase in ISA Store |
| ISASecure-130 Product Family Policy | Available for Purchase in ISA Store |
Certification Requirements Specifications for ICSA (Four Assessment Categories SDLPA, SDA, FSA, VIT)
| ICSA-311 Functional Security Assessment for IIoT Components | Available for Purchase in ISA Store |
| ICSA-312 Security Development Artifacts for IIoT Components | Available for Purchase in ISA Store |
| SSA-420 Vulnerability Identification Test (VIT) Specification | Available for Purchase in ISA Store |
| ISDLA-312 Security Development Lifecycle Assessment for ICSA | Available for Purchase in ISA Store |
| ICSA-500 Commonly Accepted IIoT Practices | Available for Purchase in ISA Store |
| SDLA-100 ISASecure Certification Scheme | View / Download PDF |

